Sunday, July 21, 2024
I just figured out why our country is in danger
Sunday, June 2, 2024
people can remain irrational longer than you can remain sane
Thursday, March 12, 2015
How to install Googlebar for Firefox 35 and beyond
googlebar could not be installed because it is not compatible with Firefox 36.0.1
It looks like we die-hard users of googlebar are now forced to use Googlebar Lite, but what I miss most about googlebar is typing whatever you want to search on, and performing your favorite google searches in just one click, whereas with Googlebar Lite, at least in the cursory examination I have given it, your favorite google searches are two clicks away.
Thanks to a suggestion from my friend David McIntyre in his comment below, rather than editing an XML file, I recommend installing Nightly Tester Tools, which helps to make googlebar compatible with the latest Firefox upgrades, almost without a hitch. However, what I found is that occasionally, Nightly Tester Tools, when upgrading googlebar to the latest version of Firefox, works for a little bit, but for whatever reason your browser crashes, resulting in googlebar disappearing, so I had to use the instructions below.
Those of us who use the Firefox add-on Googlebar know it is one of the best interfaces on Firefox to Google, "with an emphasis on easy access to many types of specialized searches". The problem is, the maintainers, John Woods, Andy Boughton, and Francis Turner, don't seem to stay on top of the version changes; while the add-on is a very useful tool, the maintainers don't seem to be very useful when it comes to applying an incredibly simple fix, so that Googlebar can be installed on the latest version of Firefox. We will now correct their oversight:- Right-click on the following link and "Save Link As..." to download Googlebar 0.9.20.05 locally to your computer:
https://addons.mozilla.org/firefox/downloads/latest/33/addon-33-latest.xpi?src=addondetail
If you simply click on the link, your browser will try to install it, and the attempt may fail. - What you downloaded has a file extension of xpi, Cross Platform Install, which is basically a package of files that has been compressed. What we want to do now is decompress the xpi, in order to access a file inside named install.rdf. Since xpi is a compressed file, you can easily decompress it, using your operating system's default decompressor, by changing the file extension from .xpi to .zip. Then you click on the renamed file to display its contents, and open install.rdf with a text editor.
- Scroll down the file, and look for the section for Firefox:
<!-- Firefox -->
In the line that says maxVersion:
<em:targetApplication>
<Description>
<em:id>{ec8030f7-c20a-464f-9b0e-13a3a9e97384}</em:id>
<em:minVersion>2.0</em:minVersion>
<em:maxVersion>5.*</em:maxVersion>
</Description>
</em:targetApplication><em:maxVersion>5.*</em:maxVersion>
replace 5.* with the latest version of Firefox, which, as of today, is 34.* - Save the install.rdf file, and add it back to the zip file.
- Rename the file extension, from zip, back to xpi.
- In your browser, click Firefox, Add-ons, Gear button, "Install Add-on From File..." and install the xpi file that you just modified.
Thursday, November 7, 2013
Be Very Careful When Selling Your Digital Goods on eBay
http://www.ebay.com/sch/Coins-Paper-Money-/11116/i.html?clk_rvr_id=390780746032&_nkw=bitcoin
 The crux of my argument is that I had created four separate listings to sell my digital goods, and during that entire time, eBay never once warned me, or anyone else who lists digital goods for sale, that doing so could result in the eBay seller being doubly damaged, meaning, the eBay seller could lose both the item being offered for sale, and the money paid for said items. I told the commissioner that eBay benefits from sales of prohibited items (and upon further analysis, even encourages sales of prohibited items), and eBay does not provide adequate safeguards to protect eBay users who are vendors and sellers.
How eBay deals with eBay users who sue eBay:
The crux of my argument is that I had created four separate listings to sell my digital goods, and during that entire time, eBay never once warned me, or anyone else who lists digital goods for sale, that doing so could result in the eBay seller being doubly damaged, meaning, the eBay seller could lose both the item being offered for sale, and the money paid for said items. I told the commissioner that eBay benefits from sales of prohibited items (and upon further analysis, even encourages sales of prohibited items), and eBay does not provide adequate safeguards to protect eBay users who are vendors and sellers.
How eBay deals with eBay users who sue eBay:
- eBay has a paralegal attempt to contact you to dismiss the case in your county, and refile in Santa Clara County, where eBay headquarters is, and where eBay hopes to have home field advantage. In Santa Clara County, the commissioners or pro-tem judges who you appear before will likely be unfamiliar to you as plaintiff, but more likely to be familiar to the eBay legal team. eBay then sends legal documents to your home county, arguing the motion for change of forum from your home county to Santa Clara County, and in my case, the commissioner decided in eBay's favor.
- eBay points to their User Agreement which states that in matters of contention, you agree to file in Santa Clara County, and that you also agree that sales of digital goods are prohibited.
- eBay is saying that they have proof an unauthorized third party accessed the eBay buyer's account (please keep in mind that the eBay buyer is claiming his eBay, Paypal, AND personal email accounts were all compromised by this unauthorized third party) and bid on my items without the account holder's permission, but eBay won't tell me what this evidence is, let alone, let me examine this evidence. I am simply supposed to take eBay at their word.
- even if what ebay is saying about the compromised accounts is true, there was a time window of 24 hours between when the item in question was first purchased by the buyer, and when eBay notified me that the buyer account was accessed by an unauthorized third party. Why didn't eBay let me know sooner, if they had evidence that the buyer's eBay, Paypal and email accounts had been compromised?
- when I was creating the listings, why didn't eBay warn me that my digital goods, and what I paid for them, and could sell them for, could potentially all be lost, and unrecoverable, and that digital goods auction listings were not covered by eBay or Paypal?
- Paypal says that if you receive payment for an item, you are covered by Paypal seller protection; you only need to provide proof of shipping, and that you sent the item to an address that is verified by Paypal. However, this protection does not cover digital goods, even though I have the evidence to show I sent the items and the buyer received them.
- when it comes to high value transactions, eBay can set up an escrow system, just like it does for eBay Motors, where a disinterested third party, perhaps an eBay employee, can make sure that the buyer is who he or she says s/he is, and that the seller actually has said goods and they are the value claimed by the seller, before payment is released and goods are delivered, as overseen by the third party.
Friday, November 30, 2012
What is a Privacy Policy, and Why Do I Need One?
You know girls, they get jealous, and sometimes they threaten each other on email.As Dr. Hillman explains below:
When the US government decides it wants some information, and there is a law enforcement basis for getting that information, email is a very easy-to-get-into source of private data...the government just has to ask the Internet service provider, like Google, for instance, these were Gmail accounts in this case, that the information came from, they just have to ask, and the ISP generally complies, if they consider it a reasonable request...You only go in front of a judge if you have to get a warrant, and right now we have a dated scheme of privacy protections that are in the Electronic Communications Privacy Act, which is a 1986 law. Right now, the way it's being interpreted by the courts, if an email is older than 6 months, there's no need to get a warrant from a judge. In that case, the FBI agent has the authority to make the decision, subject to the support of supervisors, depending on the extent of the resources that would be devoted to that. Information, if it's older than 6 months, is deemed not protected in the same way that other communications would be.In this Age of Technology, companies like Google, Facebook, Apple, Amazon and Microsoft have moved up right alongside Ma Bell and its many Baby Bells in terms of the amount of information they have about how you use their equipment to try and communicate with others. These companies, along with Internet Service Providers like AT&T, Comcast, Time Warner Cable Internet, Verizon and many others, make the landscape more complex as to who has personal information about you, whether you have access to that information or not, and which information can be unlocked by a government agency requesting records and all the data associated with you. In many ways, Ma Bell's physical telephone network has evolved and been elevated from land to sky, expanding into "the cloud", as it were, encompassing the Internet and cell phone networks. Your usage of corporate products like free email and mobile devices can reveal so much more about you than a log of when phone calls were made and to what numbers. With these corporations in possession of such intimate information about you, your activities and behavior are very important when you understand under certain circumstances that information may be shared with other people. A privacy policy covers what happens with the information you entrust others with, and to a lesser extent, what will you do with the information people entrust you with. My privacy policy for all users of my blog is, I will never share unique, identifying information about you with anyone, unless law enforcement presents me with a subpoena. However, since my blog is hosted with Google, if the government wanted information about any of my visitors, I would imagine they'd skip me and go straight to the source, to Google. Which leads me to my final, unsettling point. All our privacy concerns and handwringing over privacy policies may be moot, because everything we do and say may already be in the hands of the government. After 9/11, according to Wikipedia:
A January 16, 2004 statement by [Mark Klein, a retired AT&T communications technician] includes additional technical details regarding the secret 2003 construction of an NSA-operated monitoring facility in Room 641A of 611 Folsom Street in San Francisco, the site of a large SBC phone building, three floors of which are occupied by AT&T. According to Klein's affidavit, the NSA-equipped room uses equipment built by Narus Corporation to intercept and analyze communications traffic, as well as perform data-mining functions.According to Frontline:
The Patriot Act took our proposals to update surveillance authorities, and then it doubled or tripled those, and it took our proposals to update privacy protections for e-mail and such and took those out. So many of the same issues we had discussed at great length during the Clinton administration, had proposed in many instances to Congress, but my concern was it was an unbalanced package. It was all surveillance and no updating to protect civil liberties. And when you say it took your proposal, the guts of the Patriot Act, in terms of electronic surveillance and wiretapping and eavesdropping, what did it do? The Patriot Act did various things. Some of it was updating from a telephone-era language to Internet language. So before the wiretaps affected devices, but maybe we couldn't do wiretaps with software. Well, that didn't make sense anymore in the Internet age -- hardware, software, they should be the same.
...
What was your reaction to the warrantless wiretapping program that the president conceded existed? This was enormous news. When The New York Times told us about the NSA wiretap program, for people like me, it was as though there was this alternate universe. We had thought we had a legal system and we knew what the moves were, and it turns out that the NSA was doing something entirely outside of that. And yet the president says, "I authorized that." As a lawyer, as somebody who specialized in information technology and the law for a quarter of a century, what's your bottom-line take on this? I was outraged. I tend to be fairly level in the way I approach things, and I had a sense of outrage that they would just disregard the law. The law said the exclusive authority for wiretaps were these other statutes, and the president looked at exclusive authority and said, "Except when I feel like it." It was as though the lessons of Watergate had been forgotten. It was as though the lessons of centralized executive power and the problems that come with that had been forgotten. And now the president just said, "I think I can do it my way." So you're saying the president violated the law? My view is that the president violated the law, yes.
Wednesday, October 31, 2012
how to find out who's been watching you and how to start watching them
 Someone, whose identity was unknown to me, had typed my name into a search engine, clicked on one of the search result links, loaded my blog on their computer, and had proceeded to go through the stuff I had written. In the interest of full disclosure, finding out who is watching you is much easier when your name is unique; I know of no one else on the internet who has the same first AND last name as I do. If your name is not unique, you cannot be certain that the person who typed the words into the search engine is looking for you; the search engine user may have happened upon your website while looking for someone else, and got interested in you or what you had to say. But once my mind came to grips with the fact that somebody had conducted an online search of me, I formed a theory that the person doing research on me was either the party I was suing, or connected with the lawsuit, or associated with the attorney for the party I was suing. A few days later, I happened to be at a local courthouse, at the registrar of voters, trying to find out how to get a mail-in ballot sent to me. Afterwards, it occurred to me that if I was curious to see the latest developments in a court case involving me and another party, and I wanted to search the database of lawsuits that had been filed in the very county that I happened to be in, to see how my lawsuit was progressing, the place that I'd want to be is at a courthouse in the county where the lawsuit was filed. I asked around, inquired at the information desk, and was directed to the courthouse Records department. There, I saw a few computers that members of the general public can sit in front of and type in keywords to look up court records. After I conducted my own search on the name of the party I was suing, I confirmed that on the day my name was used as a search term by an unknown person or persons, the party I was suing, i.e., the defendant, had gotten served with the papers containing the text of the lawsuit in which I was plaintiff. While I cannot be 100% certain, I think there's a high probability that said party, after having been served with court papers, had gone online to find out more about me. The next week, I was at my attorney's office and I confirmed that my attorney's process server had traveled to the city where the GA report had indicated the online search may have originated, and served the defendant. In the next few weeks, the GA report indicated that my name was used twice more as a search term, but in both cases, the searches originated from a city that court records told me the defendant's attorney had his office. This could all just be a coincidence, of course, but I also think there's a high probability that the lawyer for the defendant may have conducted an online search of me, wanting to look through what I had written, perhaps in an attempt to find out anything that could be used to hurt my legal case against the attorney's client.
While a trip downtown to the courthouse may be fun, if you have an interest in the proceedings of a legal case, you can just as easily get updates from the comfort of your own home. You simply locate the website for the county courthouse that your lawsuit was filed in, and as long as you have the case number, or you know the date the case was filed, you can use the courthouse website to see how your (or anyone else's) legal case is progressing. However, perhaps because of privacy concerns, you cannot go online and perform a keyword search through county court records; you still need to physically be present in front of a county courthouse computer in order to search by a party's name.
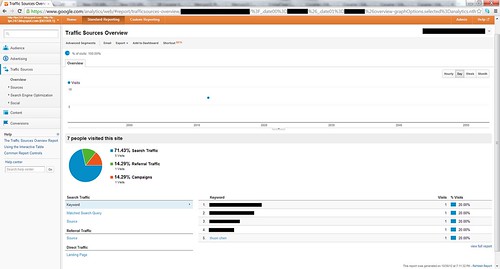
On November 1, 2011, Google put into place a new feature of their evolving privacy policy; if a person typing keywords into Google's search engine is using a browser that is already logged into a Google account, Google no longer discloses the keyword search terms on your GA report. Therefore, if you now perform a search for my name on Google while logged into your Google account, and say you visit my blog, if I were to use GA to generate my blog's traffic analysis report, my name as a keyword would no longer be visible to me. What I'd see, instead of my name, is Keyword (not provided):
Someone, whose identity was unknown to me, had typed my name into a search engine, clicked on one of the search result links, loaded my blog on their computer, and had proceeded to go through the stuff I had written. In the interest of full disclosure, finding out who is watching you is much easier when your name is unique; I know of no one else on the internet who has the same first AND last name as I do. If your name is not unique, you cannot be certain that the person who typed the words into the search engine is looking for you; the search engine user may have happened upon your website while looking for someone else, and got interested in you or what you had to say. But once my mind came to grips with the fact that somebody had conducted an online search of me, I formed a theory that the person doing research on me was either the party I was suing, or connected with the lawsuit, or associated with the attorney for the party I was suing. A few days later, I happened to be at a local courthouse, at the registrar of voters, trying to find out how to get a mail-in ballot sent to me. Afterwards, it occurred to me that if I was curious to see the latest developments in a court case involving me and another party, and I wanted to search the database of lawsuits that had been filed in the very county that I happened to be in, to see how my lawsuit was progressing, the place that I'd want to be is at a courthouse in the county where the lawsuit was filed. I asked around, inquired at the information desk, and was directed to the courthouse Records department. There, I saw a few computers that members of the general public can sit in front of and type in keywords to look up court records. After I conducted my own search on the name of the party I was suing, I confirmed that on the day my name was used as a search term by an unknown person or persons, the party I was suing, i.e., the defendant, had gotten served with the papers containing the text of the lawsuit in which I was plaintiff. While I cannot be 100% certain, I think there's a high probability that said party, after having been served with court papers, had gone online to find out more about me. The next week, I was at my attorney's office and I confirmed that my attorney's process server had traveled to the city where the GA report had indicated the online search may have originated, and served the defendant. In the next few weeks, the GA report indicated that my name was used twice more as a search term, but in both cases, the searches originated from a city that court records told me the defendant's attorney had his office. This could all just be a coincidence, of course, but I also think there's a high probability that the lawyer for the defendant may have conducted an online search of me, wanting to look through what I had written, perhaps in an attempt to find out anything that could be used to hurt my legal case against the attorney's client.
While a trip downtown to the courthouse may be fun, if you have an interest in the proceedings of a legal case, you can just as easily get updates from the comfort of your own home. You simply locate the website for the county courthouse that your lawsuit was filed in, and as long as you have the case number, or you know the date the case was filed, you can use the courthouse website to see how your (or anyone else's) legal case is progressing. However, perhaps because of privacy concerns, you cannot go online and perform a keyword search through county court records; you still need to physically be present in front of a county courthouse computer in order to search by a party's name.
On November 1, 2011, Google put into place a new feature of their evolving privacy policy; if a person typing keywords into Google's search engine is using a browser that is already logged into a Google account, Google no longer discloses the keyword search terms on your GA report. Therefore, if you now perform a search for my name on Google while logged into your Google account, and say you visit my blog, if I were to use GA to generate my blog's traffic analysis report, my name as a keyword would no longer be visible to me. What I'd see, instead of my name, is Keyword (not provided):- If your blog, like mine, is about many different topics, and the online user's keyword is (not provided) and the first page the user alights upon is your blog's landing page, instead of a specific blog post, that may be an indication that the user typed in your unique first and last name as the keyword, while using a browser that is logged into a Google account.
- If your blog URL is not easy to remember, such as tpc247.blogspot.com, but using the URL is how the user accesses your blog's landing page, then the source of traffic to your blog's landing page is direct; this is an indication that the user typed your blog URL (or at least the first few letters of the URL) into the browser's address bar and pressed 'Enter', or the user has your blog in his or her browser bookmarks. Another possibility is that the user may have searched for your unique name, copied and pasted the blog's URL from the search results into the browser address field, then pressed 'Enter', possibly in order to evade detection by GA.
Sunday, September 30, 2012
How To Execute Javascript in Firefox 6 and Beyond
Remove everything from the address bar and paste in the following and hit enter.This may not apply to other browsers, but if you use Firefox, the information provided by Mr. Yang is no longer applicable, and Step 2 is obsolete. In the latest versions of Firefox (as we go to press, we are at Firefox 15.0.1), if you try to run the Javascript snippet in the address bar, nothing will happen, and you may see
pagetracker is not definedAccording to Mozilla, the makers of Firefox, after Firefox 6, "javascript in the url-bar runs with a null security principal for security reasons". The workaround is to visit your website or application that already has the GA tracking code, then in your browser, click on Firefox / Web Developer / Web Console, and in the command line, execute or run your Javascript there. After Firefox 6, you can no longer run Javascript from the address bar. If you don't have a creation or work that has the GA tracking code enabled, and you're here to find out how to avoid being tracked altogether, may I suggest that, instead of trying to avoid GA, you can retain some of your privacy, but still give us, the people who labor in the kitchen to make the food that you eat, a consolation prize, which is a bit of information about your visit; in a previous blog post, we show how you can use Tor to browse the web; once you close the Tor browser, you erase any evidence of previous visits and avoid being tracked between browsing sessions. Gentle reader, thank you for your continued patronage.


